- cross-posted to:
- privacyguides@lemmy.one
- cross-posted to:
- privacyguides@lemmy.one
Signal has announced new functionality in its upcoming beta releases, allowing users to transfer messages and media when linking their primary Signal device to a new desktop or iPad. This feature offers the choice to carry over chats and the last 45 days of media, or to start fresh with only new messages.
The transfer process is end-to-end encrypted, ensuring privacy. It involves creating a compressed, encrypted archive of your Signal data, which is then sent to the new device via Signal’s servers. Despite handling the transfer, the servers cannot access the message content due to the encryption.
With the introduction of a cross-platform archive format, Signal is also exploring additional tools for message transfer to new devices or restoration in case of device loss or damage. Users can begin testing this feature soon, with a wider rollout expected in the coming weeks.


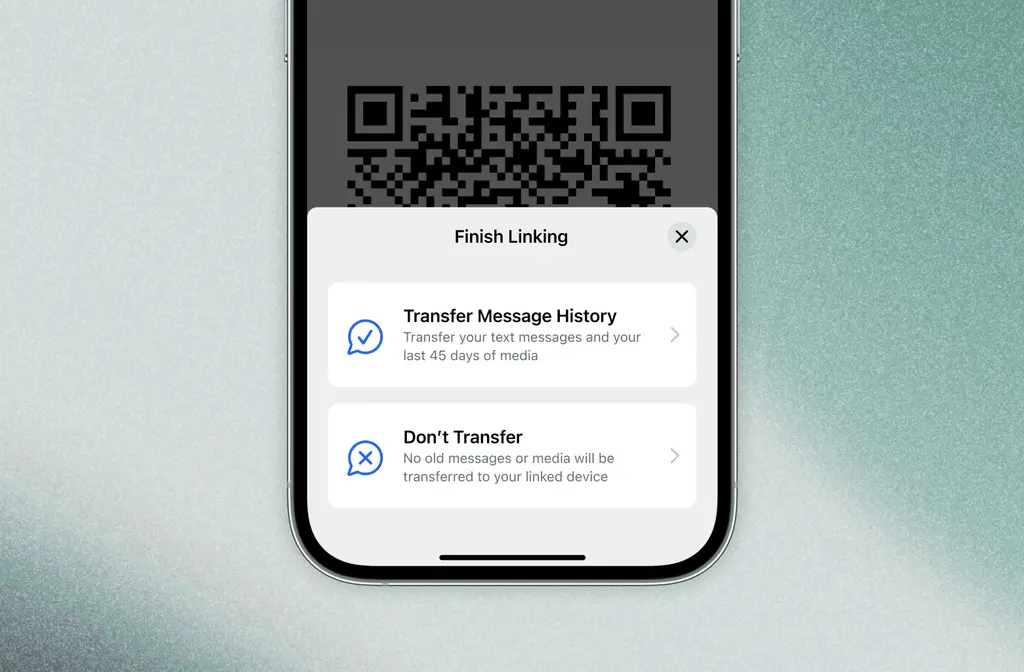
Convenience mostly, privacy needs to be convenient and easy for people, otherwise no one uses the tools.
This absolutely expands the threat surface in a few different ways though. It’s relatively low stakes, but it’s non zero. I have not dug into the implementation but I am curious how this doesn’t technically violate forward secrecy. A single session key will ostensibly be used to encrypt the entire session key database? Which means if that key is compromised in transit then the entire key history is compromised. Using the long term secret directly for data in transit is definitely not compliant either.
Surely when the chats are on-device they are not encrypted, or encrypted separately with an unrelated secret in storage which can be passed to another device?